Certified Cybersecurity Technician(C|CT) 212-82 Real Exam Dumps Online
The EC-Council Certified Cybersecurity Technician(C|CT) 212-82 exam is actually an important exam to provide individuals starting their careers in IT and cybersecurity with a certification that validates their hands-on technical skills. DumpsBase understands you clearly, we have released EC-Council 212-82 real exam dumps online, which are very helpful for the professional participants to show and validate their skills and knowledge about the Certified Cybersecurity Technician (C|CT) advanced technology and solutions. You could take EC-Council CCT 212-82 exam with complete confidence and also can obtain the best result in display in the future. With EC-Council 212-82 real exam dumps, you could pass Certified Cybersecurity Technician (C|CT) exam and could consider including your resume and obtaining the best result for finding an excellent job in the future.

What is the Certified Cybersecurity Technician(C|CT) certification?
IT students and professionals can get the important Certified Cybersecurity Technician(C|CT) certification by passing the 212-82 exam. The EC-Council Certified Cybersecurity Technician(C|CT) certification is an entry-level cybersecurity program to address the global demand for a qualified cybersecurity workforce. It is the world's only baseline cybersecurity program, which provides total foundational cybersecurity domain coverage with key concepts in each domain combined with practical hands-on labs and critical thinking challenges producing world-class cyber security technologists.
Earning the EC-Council CCT certification will benefit you including :
1. pave the way for a promising career in the realm of cybersecurity
2. teach the fundamental knowledge that cybersecurity professionals need:
● Information security
● Network security
● Computer forensics
● Risk management
● Incident handling
● Industry best practices
3. improve employability by validating certification holders’ skills as cybersecurity specialists who can strengthen organizational security
4. provides extensive opportunities to practice the hands-on skills necessary for any technical role involving administrative privileges and cybersecurity considerations
How to pass the 212-82 Certified Cybersecurity Technician(C|CT) exam successfully?
You can choose to pass the EC-Council 212-82 exam and earn the Certified Cybersecurity Technician(C|CT) certification. It will allow you to eventually grow your skills into various roles, including penetration testing, security consulting, auditor and administrator roles, and beyond. It establishes a foundation of technical skills required to create successful technologists who will advance across various work roles.
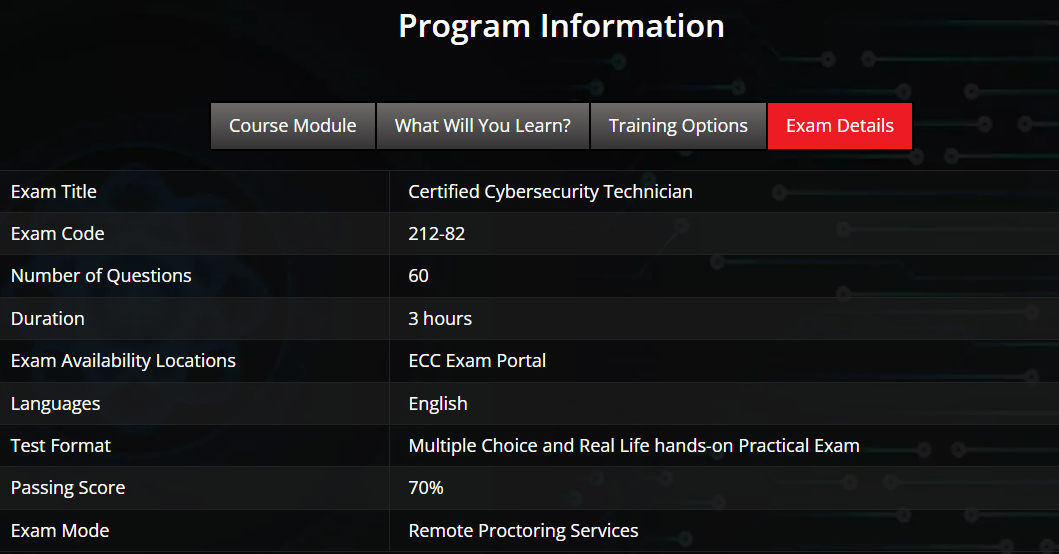
Based on the actual 212-82 exam details and objectives, we DumpsBase have the EC-Council 212-82 real exam dumps online. Students and professionals can visit DumpsBase to choose the EC-Council 212-82 exam dumps in order to get themselves registered for the Certified Cybersecurity Technician (C|CT). Certified Cybersecurity Technician (C|CT) candidates can get the details as well as 212-82 exam by referring to the official website of EC-Council. Certified Cybersecurity Technician (C|CT) 212-82 exam candidates can get help from DumpsBase EC-Council 212-82 real exam dumps for preparing for the Certified Cybersecurity Technician (C|CT) 212-82 exam and getting the certification successfully.
What is the effective way to check DumpsBase 212-82 real exam dumps?
Before getting the Certified Cybersecurity Technician (C|CT) 212-82 real exam dumps online, you may want to check the high quality. Here, we have the free EC-Council CCT 212-82 demo questions for learning first. It is an effective way to check the DumpsBase 212-82 real exam dumps.
Thomas, an employee of an organization, is restricted to access specific websites from his office system. He is trying to obtain admin credentials to remove the restrictions. While waiting for an opportunity, he sniffed communication between the administrator and an application server to retrieve the admin credentials. Identify the type of attack performed by Thomas in the above scenario.
A. Vishing
B. Eavesdropping
C. Phishing
D. Dumpster diving
Answer: B
Myles, a security professional at an organization, provided laptops for all the employees to carry out the business processes from remote locations. While installing necessary applications required for the business, Myles has also installed antivirus software on each laptop following the company's policy to detect and protect the machines from external malicious events over the Internet.
Identify the PCI-DSS requirement followed by Myles in the above scenario.
A. PCI-DSS requirement no 1.3.2
B. PCI-DSS requirement no 1.3.5
C. PCI-DSS requirement no 5.1
D. PCI-DSS requirement no 1.3.1
Answer: C
Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool to discover the OS of the target system. As a result, he obtained a TTL value, which Indicates that the target system is running a Windows OS. Identify the TTL value Henry obtained, which indicates that the target OS is Windows.
A. 64
B. 128
C. 255
D. 138
Answer: B
In an organization, all the servers and database systems are guarded in a sealed room with a single entry point. The entrance is protected with a physical lock system that requires typing a sequence of numbers and letters by using a rotating dial that intermingles with several other rotating discs.
Which of the following types of physical locks is used by the organization in the above scenario?
A. Digital locks
B. Combination locks
C. Mechanical locks
D. Electromagnetic locks
Answer: B
An MNC hired Brandon, a network defender, to establish secured VPN communication between the company's remote offices. For this purpose, Brandon employed a VPN topology where all the remote offices communicate with the corporate office but communication between the remote offices is denied.
Identify the VPN topology employed by Brandon in the above scenario.
A. Point-to-Point VPN topology
B. Star topology
C. Hub-and-Spoke VPN topology
D. Full-mesh VPN topology
Answer: C
RAT has been setup in one of the machines connected to the network to steal the important Sensitive corporate docs located on Desktop of the server, further investigation revealed the IP address of the server 20.20.10.26. Initiate a remote connection using thief client and determine the number of files present in the folder.
Hint: Thief folder is located at: Z:\CCT-Tools\CCT Module 01 Information Security Threats and Vulnerabilities\Remote Access Trojans (RAT)\Thief of Attacker Machine-1.
A. 2
B. 4
C. 3
D. 5
Answer: C
Paul, a computer user, has shared information with his colleague using an online application. The online application used by Paul has been incorporated with the latest encryption mechanism. This mechanism encrypts data by using a sequence of photons that have a spinning trait while traveling from one end to another, and these photons keep changing their shapes during their course through filters: vertical, horizontal, forward slash, and backslash.
Identify the encryption mechanism demonstrated in the above scenario.
A. Quantum cryptography
B. Homomorphic encryption
C. Rivest Shamir Adleman encryption
D. Elliptic curve cryptography
Answer: A
Tenda, a network specialist at an organization, was examining logged data using Windows Event Viewer to identify attempted or successful unauthorized activities. The logs analyzed by Tenda include events related to Windows security; specifically, log-on/log-off activities, resource access, and also information based on Windows system's audit policies.
Identify the type of event logs analyzed by Tenda in the above scenario.
A. Application event log
B. Setup event log
C. Security event log
D. System event log
Answer: C
Tristan, a professional penetration tester, was recruited by an organization to test its network infrastructure. The organization wanted to understand its current security posture and its strength in defending against external threats. For this purpose, the organization did not provide any information about their IT infrastructure to Tristan. Thus, Tristan initiated zero-knowledge attacks, with no information or assistance from the organization.
Which of the following types of penetration testing has Tristan initiated in the above scenario?
A. Black-box testing
B. White-box testing
C. Gray-box testing
D. Translucent-box testing
Answer: A
Johnson, an attacker, performed online research for the contact details of reputed cybersecurity firms. He found the contact number of sibertech.org and dialed the number, claiming himself to represent a technical support team from a vendor. He warned that a specific server is about to be compromised and requested sibertech.org to follow the provided instructions. Consequently, he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical Information to Johnson's machine.
What is the social engineering technique Steve employed in the above scenario?
A. Quid pro quo
B. Diversion theft
C. Elicitation
D. Phishing
Answer: A
